Matchless Info About How To Build A Honeypot

Learn how to build a honeypot that will trap attackers and gather data on what they're doing to help secure your network against future attacks.
How to build a honeypot. Click here for the github link. Then, run the honeypot with:. How to add a honeypot to your website form.
How to make a fake device on your network to see if anyone is trying to attack or hack into it. Start by searching for the ec2 service in aws. #cybersecurity #honeypot #threatintelligence #simplycyberusing aws, intezer protect, docker
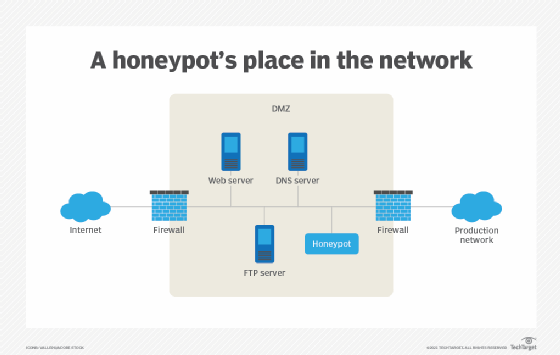
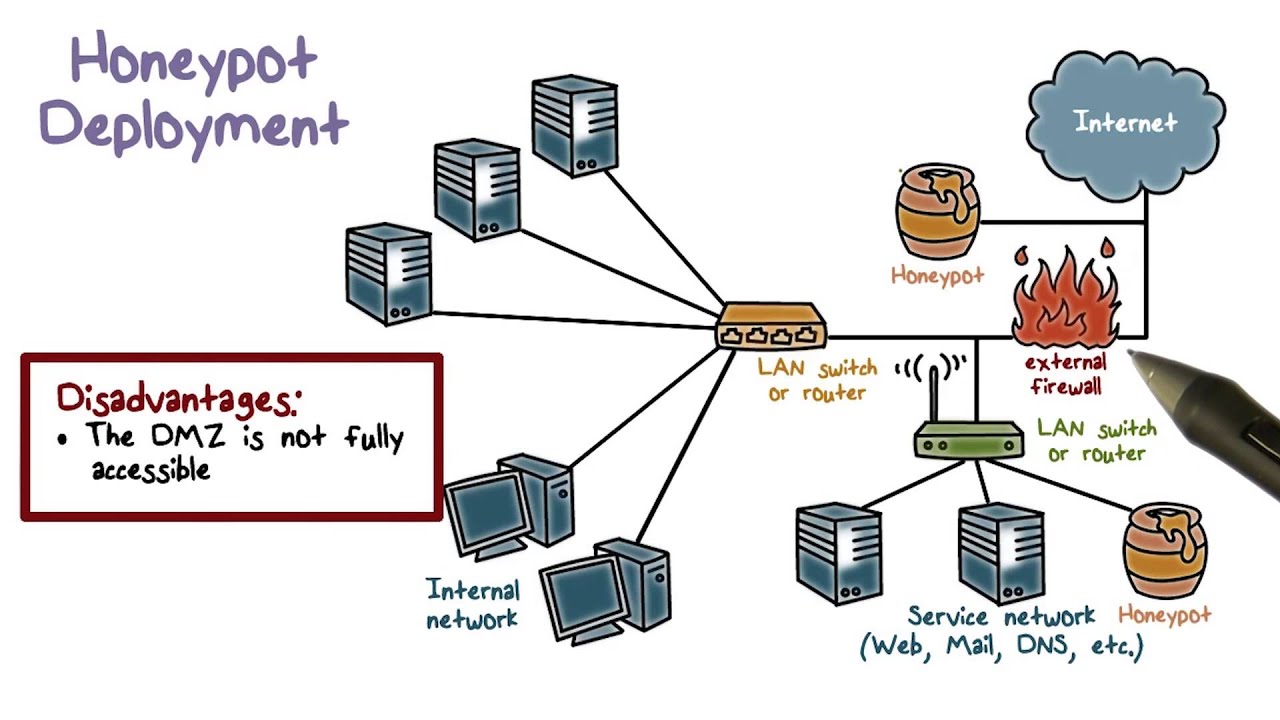
Early warning systems provide alerts. I added only the css to my wordpress honeypot installation because i have a custom built form though contact form 7 but i had to build according to the client's spec. The first step in implementing a honeypot is to create the right environment.
This code basically sets the logging. If you already have your infrastructure set up for your honeypot, you can skip this step and go to setting up detection to. Create a form so your users can subscribe to your messages;
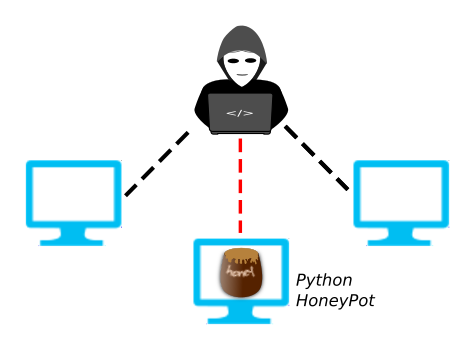
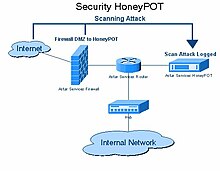
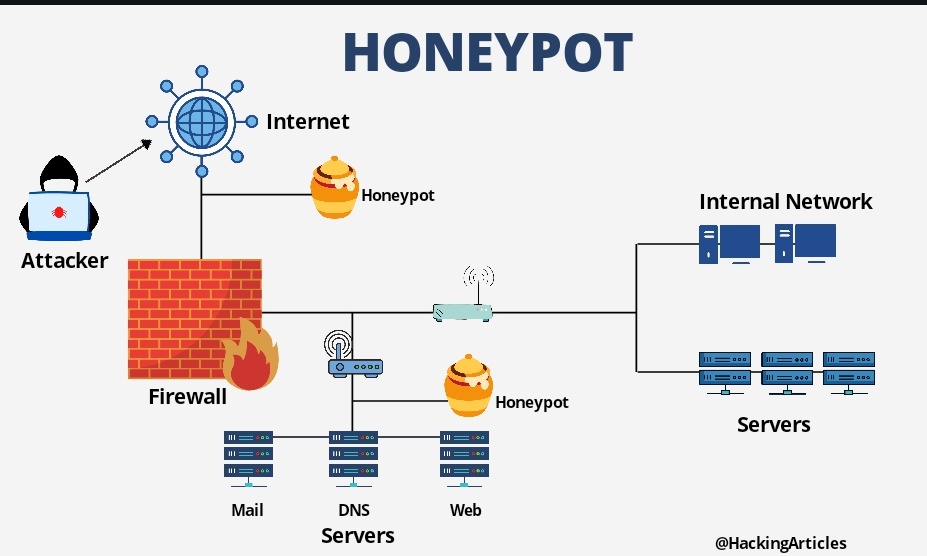
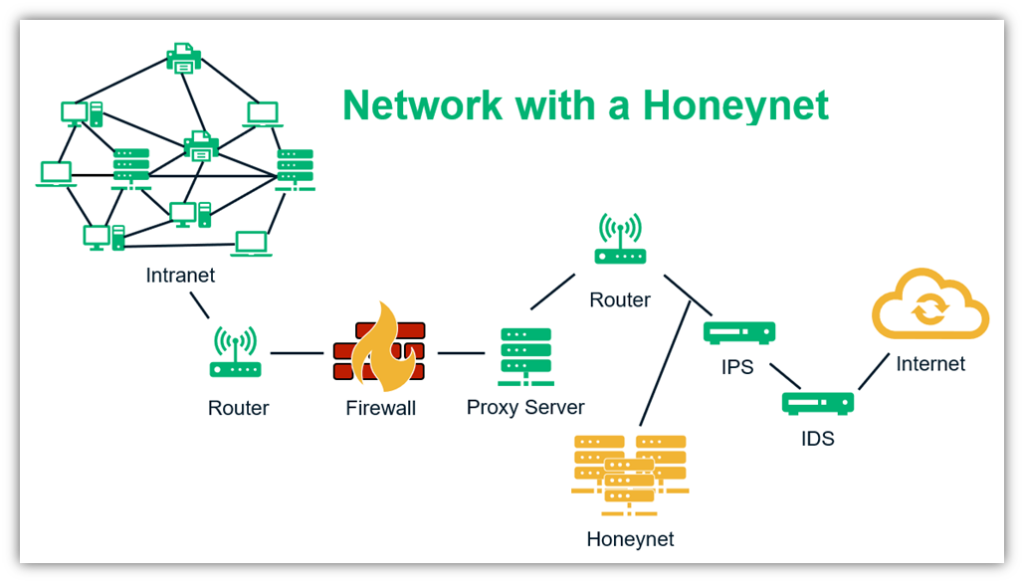
Learn to build a cyber deception honeypot in 20 minutes. We can log this with the honeypot tool, pentbox. A honeypot is a network device that tricks hackers into thinking they've broken into an organization's real network when actually they are in a fake network set up as a trap.
We can log this with the honeypot tool, pentbox. First, need a way to log the attacks our honeypot receives. Building the honeypot creating a logger.
Once you've checked all those files are in place, go ahead and build the docker images with: